A Complete Breakdown of the March 2025 Attack on Hyperliquid DEX
After its headline-making airdrop in November 2024, Hyperliquid quickly surged to the top ranks of decentralised exchanges (DEXs), overtaking heavyweights like Jupiter and dYdX. With blazing-fast transactions, zero KYC requirements, and deep liquidity pools, it became the go-to platform for crypto traders.
But in March 2025, the platform faced its biggest test yet.
On March 26, high-risk positions worth nearly $8 million were opened on Hyperliquid – positions that not only threatened the stability of the exchange but also put client assets in the Hyperliquidity Provider Vault (HLP) at risk. Behind the scenes, a series of suspicious trades and price manipulations hinted at a coordinated attack, leveraging vulnerabilities in both Hyperliquid and third-party platforms.
ExpertStack investigated the full timeline of events—analysing the attack, competitor responses, and the controversial decisions by Hyperliquid’s leadership that raised questions about decentralisation.The Day of the Attack
Hyperliquid’s risk management relies on its HLP Treasury liquidity pools. Whenever a user opens a position, the system auto-executes a hedge. If a position is liquidated, the platform gradually buys back the asset—sometimes triggering a cascade.
On March 26, this mechanism was exploited to dramatic effect.
Attackers manipulated the price of JELLYJELLY, a low-liquidity token, on external platforms, creating a domino effect inside Hyperliquid’s system. At the time, HLP had around $290 million in its vault.
Key Timeline of Events:
⏱ Phase 0: “Market Preparation”
From 10:50 to 12:15 UTC, JELLYJELLY price rose by 13%, then sharply crashed by 93%-a stress test before the main strike. The drop, from $0.1287 to $0.00831, aimed to liquidate long positions and destabilise the HLP.
⏱ Phase 1: Building a Delta-Neutral Position
At 12:53 UTC, attackers opened large short positions ($4.08M) via address 0xde95…c91, while simultaneously placing long orders ($4.06M) through addresses 0x67fe…CA2 and 0x20e8…808 to hedge losses.
⏱ Phase 2: Triggering Liquidations
Minutes later, they withdrew available margins and partially closed shorts to prompt liquidations. One short of ~$254K closed at $0.073978. Shortly after, a short position of nearly 400 million JELLYJELLY was dumped into HLP. The attackers swiftly moved ~2.76M USDC to Arbitrum – locking in a manipulated short price of $0.011282.
⏱ Phase 3: Final Blow – The Pump and Dump
From 13:00 to 14:00 UTC, they aggressively bought JELLYJELLY across external exchanges, causing a 400% price surge to $0.05. Because Hyperliquid’s oracle relied on external spot prices, this manipulation immediately impacted derivatives and triggered massive unrealised losses.
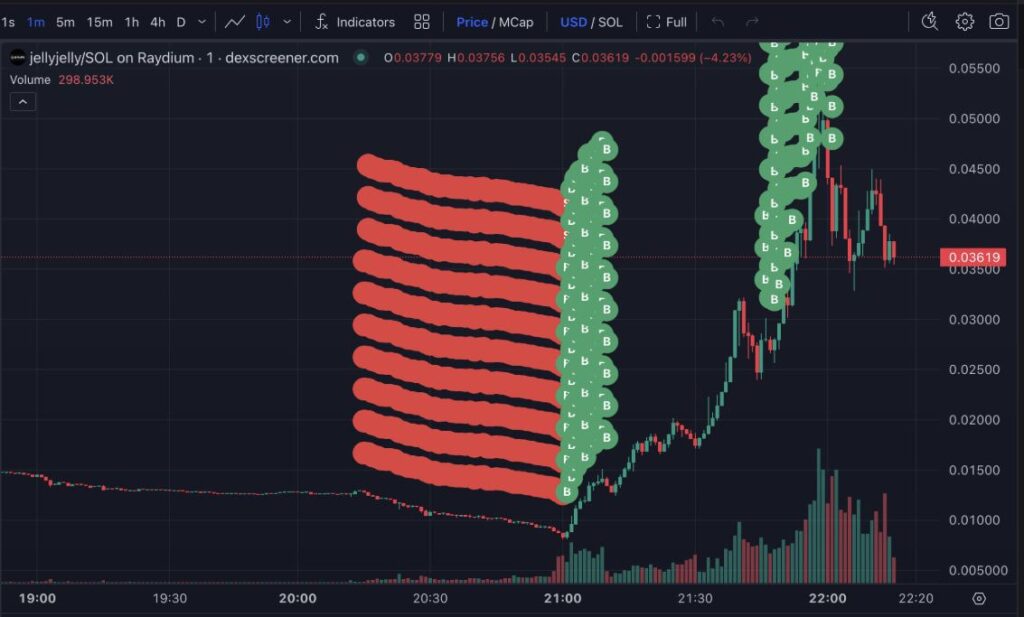
JELLYJELLY price manipulation. Source: Lookonchain, Raydium.
Earlier transactions from March 15-25, flagged by Hyperliquid analysts, appeared to be dry runs – testing liquidation triggers and order types.
The Fallout
One attacker (a “whale”) successfully withdrew about $6.2 million, while another attempt to extract an additional ~$900K failed – leading to a net loss of ~$4K.
Hyperliquid halted trading, froze the price at $0.0095, and even ended with a slight gain of ~$700K. The team pledged full reimbursements to affected users.
Yet, this damage control sparked intense criticism. Influencers and Centralised Exchange (CEX) executives accused Hyperliquid of betraying the ideals of decentralisation and acting negligently.
Could CEXs Have Handled It Differently?
By April 8, 2025, Hyperliquid was handling ~$13B in daily perpetual trading volume – over 50% of the global DEX market share, per DeFi Llama. CoinGecko listed its open interest at $2.7B, beating major players like Deribit and even CEX arms like KuCoin and Crypto.com.
Hyperliquid accepts both USDC (via Arbitrum) and Bitcoin as collateral, giving users a rare ability to trade digital gold directly from their Web3 wallets.
On March 15, it captured 21% of Binance’s and 50% of Bybit’s volume in BTC futures – remarkable for a DEX.
But Hyperliquid’s team pointed fingers. Analysis suggested Bybit played a key role in the attack:
- Oracle manipulation: Bybit’s spot data heavily influenced Hyperliquid’s margin price calculations.
- Liquidity: Bybit’s deep order books allowed significant trades without slippage.
- Market domination: With Binance not listing JELLYJELLY, Bybit’s pricing had outsized influence.
In short, attackers gamed Bybit’s data to distort Hyperliquid’s oracle.
Strategic Silence – or Not?
While manipulation happened through Bybit, other CEXs didn’t remain idle.
At 15:30 UTC, OKX listed JELLYJELLY perpetuals with 50x leverage. Binance followed at 16:00. The timing was… convenient.
Arthur Hayes, former BitMEX CEO, hinted at collusion. He cryptically framed OKX CEO Star Xu and ex-Binance chief CZ as having pounced on a weakened rival.
Hyperliquid’s Next Chapter
Despite the chaos, Hyperliquid’s core infrastructure remains strong. Built for scalability, it plans to integrate SVM and MoveVM, and leverages its custom HyperBFT consensus for potential L1 and L2 DeFi use cases.
In a March 31 interview with Wu Blockchain, LSD protocol developer Sean offered his perspective:
Binance and OKX feel threatened. They’re trying to recreate Solana-like dynamics by pushing meme tokens and onboarding users aggressively via BNB Chain.”
He also criticised influencers for disproportionately promoting CEXs and demonising Hyperliquid.
It’s fair to compete, but this narrative war is toxic. Centralised platforms aren’t saints – they have their own flaws. Their job is to enable fair trading, not run smear campaigns via influencers.”
Sean also acknowledged Hyperliquid’s shortcomings:
- Closed-source limitations raise concerns about internal manipulation (e.g., MEV).
- Insufficient blockchain transparency, such as lacking detailed account histories.
- Dutch auction listings for low-cap tokens enabled overly large short positions.
- Passive market maker design, if exploited, can lead to serious HLP losses.
The Bottom Line
The JELLYJELLY attack exposed real vulnerabilities – not just in Hyperliquid’s architecture, but in how DeFi interacts with centralised infrastructure.
More than just an isolated exploit, it was a wake-up call. It reignited debates around oracle reliance, systemic risk, and the blurry lines between CEXs and DEXs.
While Hyperliquid took swift corrective action and recovered financially, it now faces a trust battle—and a renewed mission to evolve its ecosystem without compromising its decentralised vision.
What’s next?
That’s a question the entire crypto world should be asking.